In this article we tried to give our interpretation of what is OSInt. NOW it's time to get our hands dirty with one of the first activities done in online investigations: the search for aliases and usernames used oline by a target.
Where to start
Case study: Ramingo
Let's start with this example: we received a screenshot of a Telegram user (random one, isn't it @trapper?)

We can immediately make a few initial obiservation:
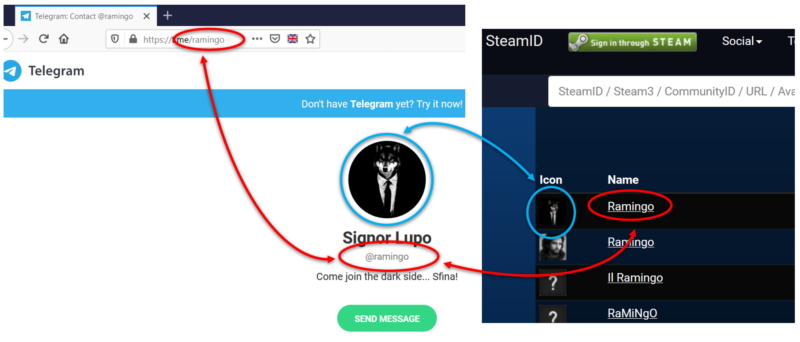
- without the need to install the Telegram client, we can see that the word ramingo, used in the username, is also in its vanity url (both circled in red).
- In this case the user has a rather singular profile picture: a wolf dressed with suit and tie (circled in blue).
- The nickname "Signor Lupo" and the bio "Come join the dark side … Sfina!" allow us to think that most likely this is an Italian user.
However, we should be kept in mind that these information are provided by the user and can be changed very often over time.
At the moment Telegram does NOT allow us to display the user's user id that identifies the users in the system in a unique way. To obtain that data, we need to interact directly with the Telegram APIs or with particular Telegram clients, such as PLUS.
After this premise, let's take a look to a few available tools to keep find information on this user.
Search engines
As trivial as it may seem, the initial sources from which we can obtain useful data or information are the search engines, such as Google and DuckDuckGo. Often, in fact, we get surprising results because aliases are one of the most commonly included data in user descriptions present in forums or in Instant Messaging services. An advanced use of dorks could provide even more meaningful results.
Another use of search engines concerns the search for profile images. Image search is a very common feature to all search engines. It oure opionion that right now Yandex offers extremely interesting image / face recognition features.
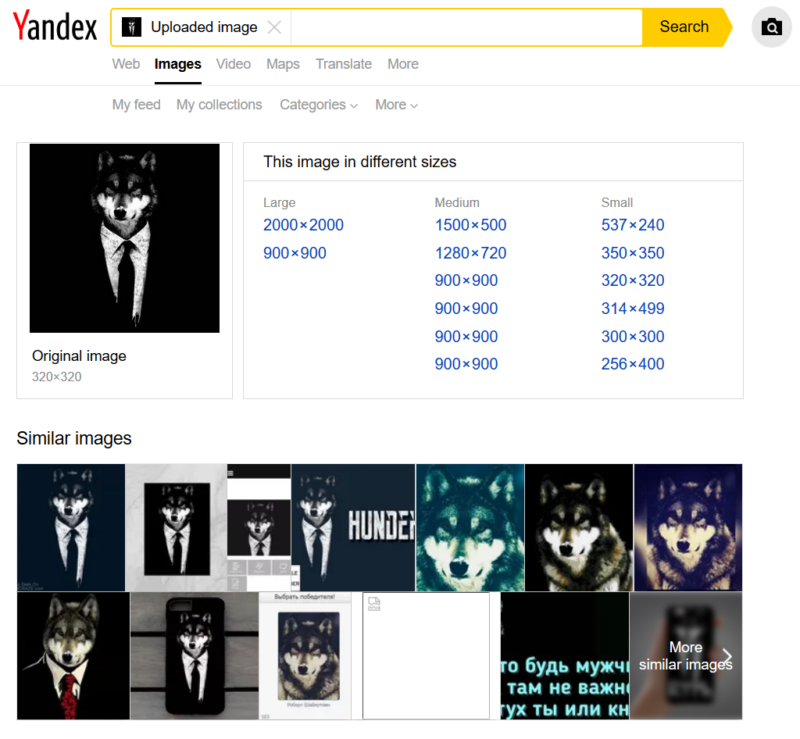
Search web services
These web services are designed to provide an indication to the user on which sites / social networks it is possible to register a specific nickname.
We'll take the opposite angle in our investigation: we will initially focus on those sites where the username has already been registered and exclude the sites and social networks where it is possible to register the username we are looking for.
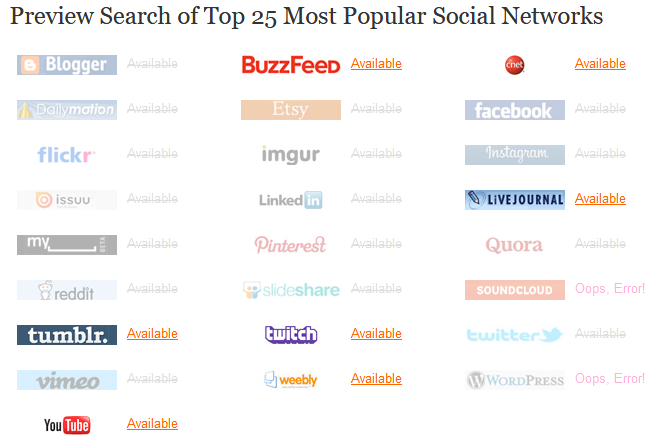
Knowem.com
knowem.com is one of the most used services for searching for usernames, within websites and social networks, also by searching for domain names and registered trademarks.


Just enter the username to search in the appropriate search box and click search to start the search for the username, in this example ramingo, on over 500 social networks, websites and domains.
Namevine.com
namevine.com allows you to search among the most popular social networks, accepting any text, even partial, as input. it's an excellent tool to start investigazions for several reasons: its extreme speed in providing results and the possibility of searching for partial texts, (i.e.: the target has slightly changed his/her username).
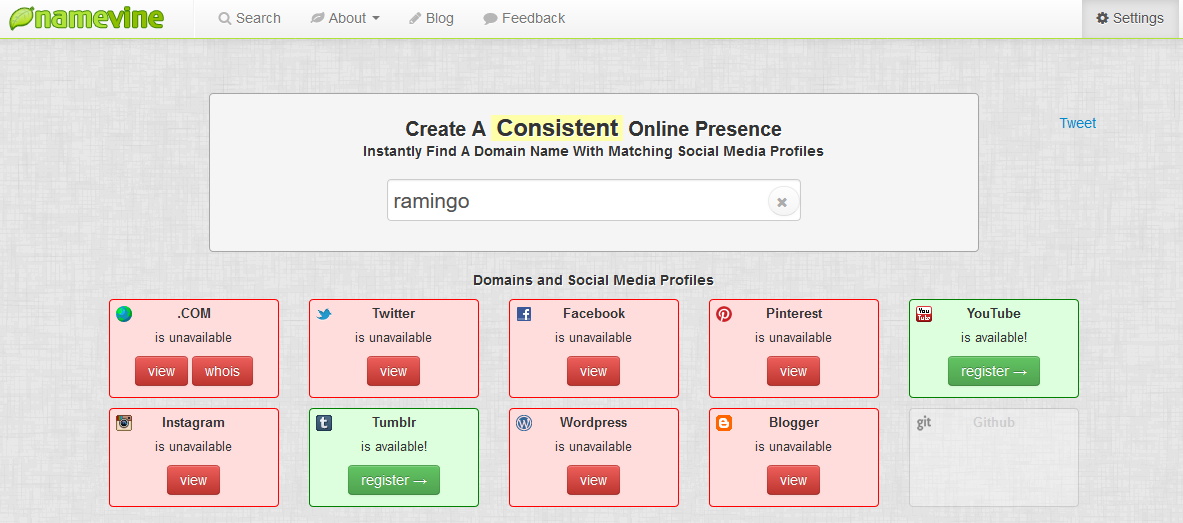
The possibility of clicking on the appropriate "View" tab to gain direct access to the profile linked to the username you are looking for will be very useful.
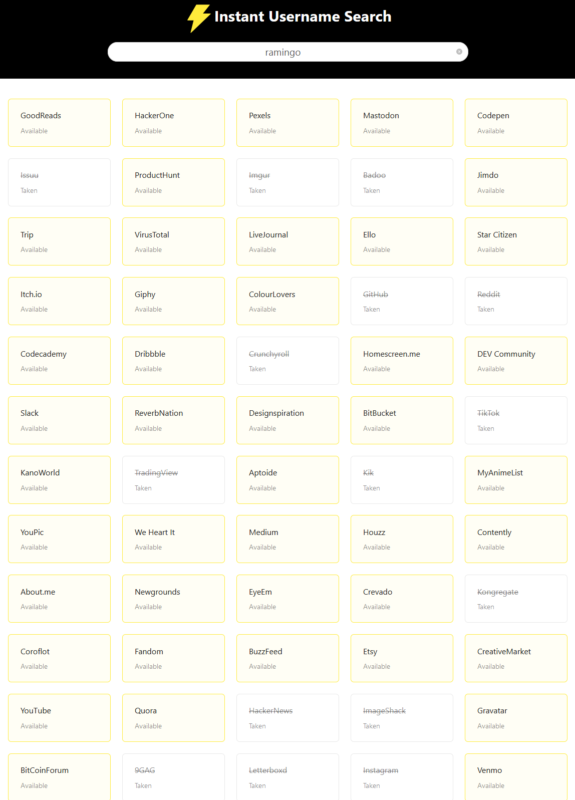
Instantusername.com
Among the many services dedicated to searching for a username, instantusername.com stands out first and foremost for its GNU GPL v.3.0 license, and for its capability of extend his search over 100 social network sites, including the very recent "Mastodon".
Command line tools
As an alternative to the services previously illustrated, it is possible to rely on some command line tools freely available online or already included in some dedicated Linux distributions, such as Tsurugi Linux. Tsurugi Linux is a completely free open-source project to which we intend to dedicate several other articles.
After starting the distribution in live mode or in virtual machine, I suggest you take advantage of the "OSINT Profile Switcher" through which you can view only the tools useful for the activities connected to the OSInt, hiding those dedicated to Digital Forensics, but leaving them available .
Among the various tools, let's see together how to use a couple of them, very useful and effective.
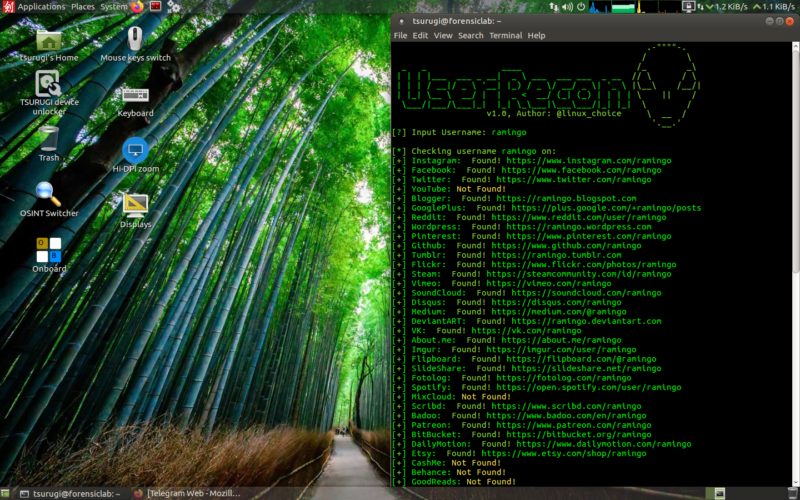
UserRecon
userRecon is a command line tool that can be started directly from the "Tsurugi - Osint" menu. Once started, a MATE terminal window will open, and you can directly enter the username to be found on over 75 websites and social networks.
At the end of the search the results will be either shown on the video, correlated by all the direct links, or automatically saved in a text file.
update: the original link is no longer reachable, it has been replaced with a working one.
Userrecon-py
userrecon-py allows you to expand the same search in almost 190 social networks and websites, returning positive feedbacks on screen.
Also in this case userrecon-py can be reached via menu: a shell will be opened in which this command has to be inserted:
userrecon-py --target USERNAME
At the end of the search, the positive results found will be listed on the screen. To get a text file containing the positive results we have to redirect the output of the script to a text file using this command:
userrecon-py --target ramingo >> userrecon-py.txt
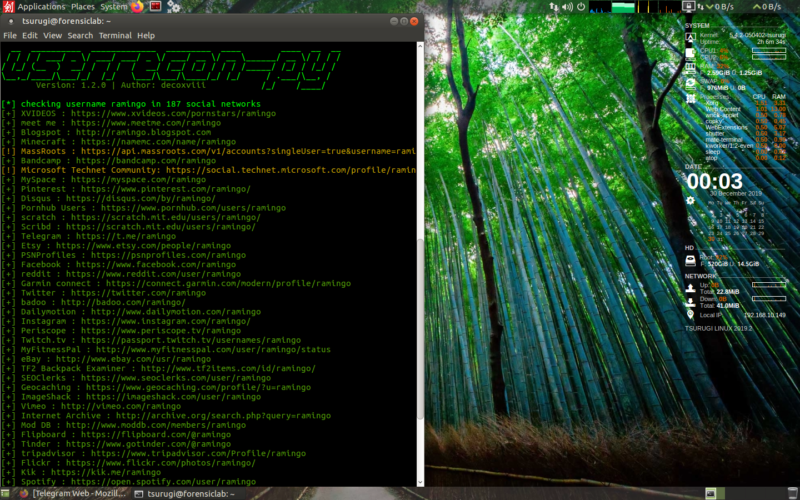
Let's start analysing the data
After collecting all this data we have to correlate it and analyse it to get the information we need.
The presence of many sites dedicated to the world of gamers stands out immediately. Although many have not provided appreciable results, it is worth dwelling on some of them:
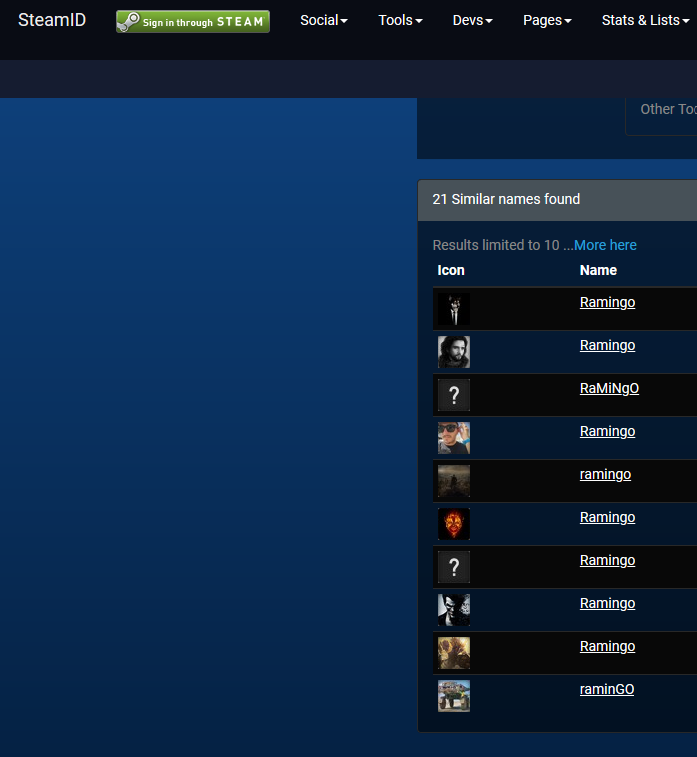
From the research carried out on the gaming platform "Steam", we note the presence of at least 21 profiles that use, at this moment, the nickname Ramingo. Checking them one by one is undoubtedly the best approach, but it takes much longer. In this case, a careful observation of the profile images could help us better focus the research on the most interesting user profile: the first uses the image of a wolf dressed with a suit and a tie.
By connecting to the user profile, we can better observe the image:
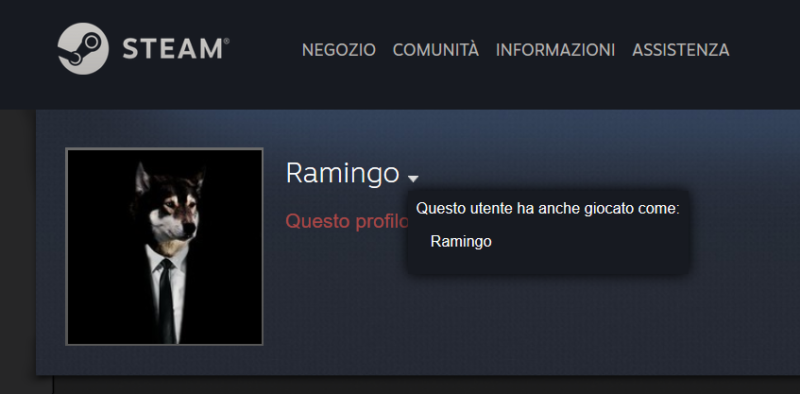
Here too we have a wolf dressed with a suit and a tie. We can assume with reasonable certainty that, given the combination of photos + username, the two accounts are attributable to the same person. The functionality of Steam "This user has also played as:" should not be overlooked because it could provide us other usernames used in the past by the user.
It should be kept in mind that this type of services offer the possibility to purchase games and hardware through the use of electronic transactions. This means that for entities with judicial power it may be possible to obtain REAL user data such as name, surname, means of payment, etc.
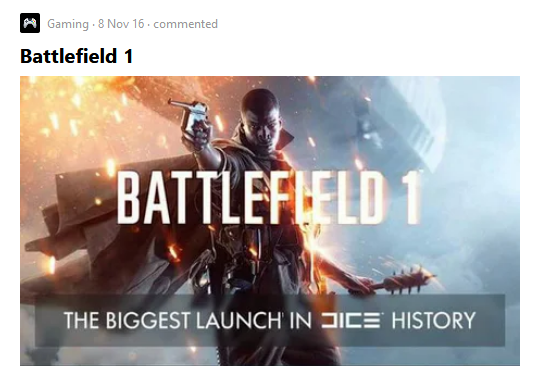
Browsing through the results provided by the previous sites and tools, a Github profile registered as ramingo also stands out:
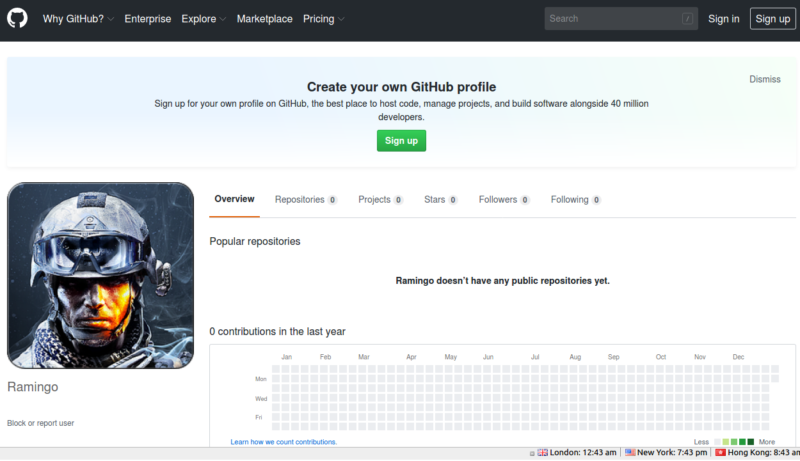
Apparently it is not immediately related to the profile sought but the presence of the profile image linked to "Battlefield 3" suggests that we need to pay more attention to it.
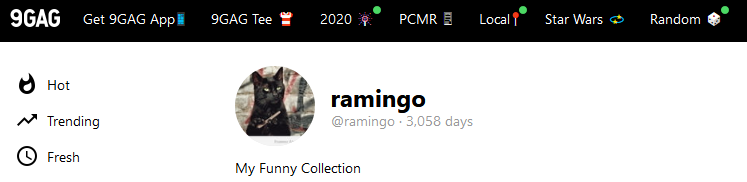
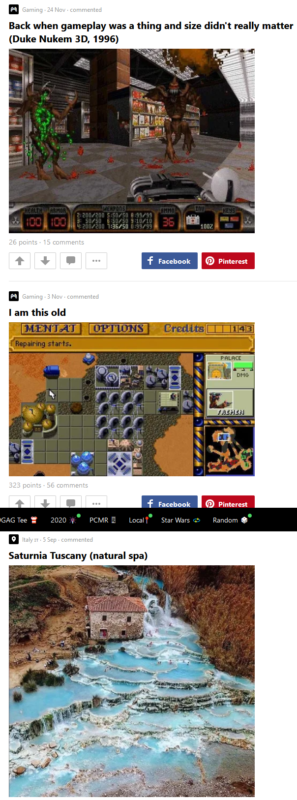
In fact, the user / gamer track provides additional insights. Our research also returned us a 9GAG ramingo user profile, which could be interesting.
What other conclusions can we draw from the previous images?
- The use of a profile image containing a humanized animal (wolf or cat that is performing a typical human activity), the numerous sections dedicated to games, the constant presence of posts referring to them (among which we find again "Battlefield") and the presence of numerous posts referring to Italy, provide sufficient elements to consider the profile worthy of further study.
- The presence of a possibly unconscious pattern adopted by the target in the choice of username or profile images.
- A rough idea of the user's hobbies useful for directing the search for other profiles.
Conclusion
In this article we gave a quick look at only two of the main methodologies for searching for a username, a preliminary and necessary activity to outline as much as possible the digital identity of a user.
It should be considered that, however, that methods such as those just illustrated, will provide a large number of false positives, especially with very common usernames, which require the adoption of methodologies and tools to validate the results.
P.S.: If you have suggestions or other articles on the same topic, please report them in the comments!
.jpg?width=50&height=50&name=1667323710771%20(1).jpg)
January 3, 2020


Comments