The article “Tracking Illicit Transactions With Blockchain: A Guide, Featuring Mueller” from Brenna Smith, published on Bellingcat's website, describes a technique used to identify a Bitcoin transaction.
The transaction is cited in a document from the Grand Court of the District of Columbia. Its exact amount is known (0.026043 equivalent to $ 9.74) and the date it was made (February 1, 2016).
The transaction, according to the document, was carried out by a group of Russian secret agents adn was intended to manipulate the work of the US Democratic National Committee and Hillary Clinton's presidential campaign.
Brenna managed to find the Bitcoin address 1LQv8aKtQoiY5M5zkaG8RWL7LMwNzVaVqR from which the transaction started by observing the content of the transaction blocks present in the blockchain on February 1, 2016.
Now, let's try to answer these two questions:
- who does this address belong to?
- are there other addresses that can be linked to this?
Executive summary
From what has been observed, we can say that a certain amount of bitcoin (11.8445) was purchased through the Cex.io exchanger, subsequently used for fairly regular payments through intermediaries such as CoinPayments.net and BitPay.com.
By reconstructing the flow of transactions and communicating the transactions of interest to the involved exchanges and intermediaries, it is possible to obtain further details on the examined actors, making use of judicial police powers unrelated to the Open Source Intelligence activities indicated below.
Analysing transacrions
In a similar analysis, first of all you have to ask yourself two questions:
- where are the bitcoins from?
- where were they sent?
To find the answer to these two questions I suggest you apply to this case the analysis technique called "flow analysis" which in this case looks a lot like the classic "follow the money" approach.
This approach should allow you to identify not so much who managed that money but rather who could provide you with some more precise information on the spins that those bitcoins made: any active exchanger or payment processor.
We turn our attention to bitcoin exchanges or payment processors because they are the ones who allow exchanges between current and virtual currency.
In order to continue their activities in compliance with the regulations of the countries in which they operate, they had to adopt the KYC procedures envisaged to limit the illicit use of money.
Then identifying these legal entities and the wallets of interest will allow law enforcement to obtain all the necessary information about their customers through the use of the tools provided by the Judicial Police.
Where are the bitcoins from?
To find an answer to this question we will use one of the many blockchain explorers available: bitcoinwhoswho.com. This service is able to provide you with additional information about the addresses you are checking (scam reports or links to web pages where they are mentioned, etc.).
In combination you can use walletexplorer.com: this service uses an algorithm to search for bitcoin addresses and associate them with others in order to reconstruct a wallet and relate the latter to known entities such as exchanges, dark markets, gambling sites, etc.
Unfortunately, in this case, the analysis of the address
1LQv8aKtQoiY5M5zkaG8RWL7LMwNzVaVqR via bitcoinwhoswho.com did not provide any additional information.

Note however that this address was involved in only two transactions: one inbound and one outbound mentioned in the article.

Not even walletexplorer.com is able to provide you with any useful information: the wallet consisting of the address being analyzed alone cannot be connected to any known name, nor is any further bitcoin address aggregated that could be associated to the same user.

Anteprima della meta descrizione:To understand where bitcoins came from, let's go back to the result provided by bitcoinwhoswho.com.
Look at the incoming transaction, indicated by the green arrow in Figure 2, and view the information available on the sender address, 1HF9VgN3AcA5RJd6ZUPnXdETmFbYmikveN.
This address also made only two transactions of which it is not possible to obtain additional information either via bitcoinwhoswho.com or via walletexplorer.com.

Let's continue by analyzing the sender address: 17aW6uemEhYGCw38g3D35Q9z9kuG3vPmED.
Again we have no luck. We just have to reconstruct the sequence of transactions, gradually identifying the senders addresses:
- 1Fj4RkrtnnMn5mBtQFW5ZkzEw4vGyCoRe9;
- 1KSkbN7JHYxBSoYwuuWuzA4dpZf9TKP6V8;
- 1AB99VvWeLtRcEZ6yubX1Cqvcvi4bPH6R6;
- 13ZMs871ZBcTTauhXDpRQ6hDaTaPcPVmTY;
- 1MS4KRpKakzTEUFzcU9PHCbs2f1u9a1aL4;
- 1MYQzejdwhiU83qy4SsLKcm7CwV5XxVFRn;
- 1ECFBdcnfhVWcGG6k4p4Pt4J9ciQsK8wEn;
- 1GN5ZGGQsgQGQdP5Yc2LAWUKssrLk5YRbc;
- 1KgUcHDuWLVzFxVnwp3u5jZw3FmorjG1jD.
If you look closely at the transactions involving the last address on the list, you can see that it receives bitcoins from four distinct addresses, unlike what we have seen so far.
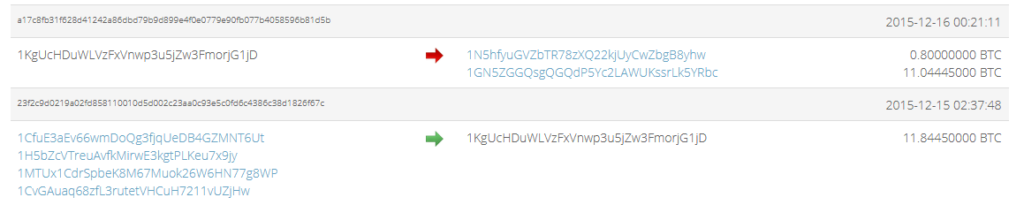
These four addresses:
- 1CfuE3aEv66wmDoQg3fjqUeDB4GZMNT6Ut;
- 1H5bZcVTreuAvfkMirwE3kgtPLKeu7x9jy;
- 1MTUx1CdrSpbeK8M67Muok26W6HN77g8WP;
- 1CvGAuaq68zfL3rutetVHCuH7211vUZjHw;
are subject to much more intense activity than the others examined so far.
Note that walletexplorer.com clusters all 4 addresses in the wallet with ID 0001d2e726, whose activities are mostly inbound transactions attributable to the Cex.io exchanger, managed by the Anglo-Saxon company Cex.io LTD.
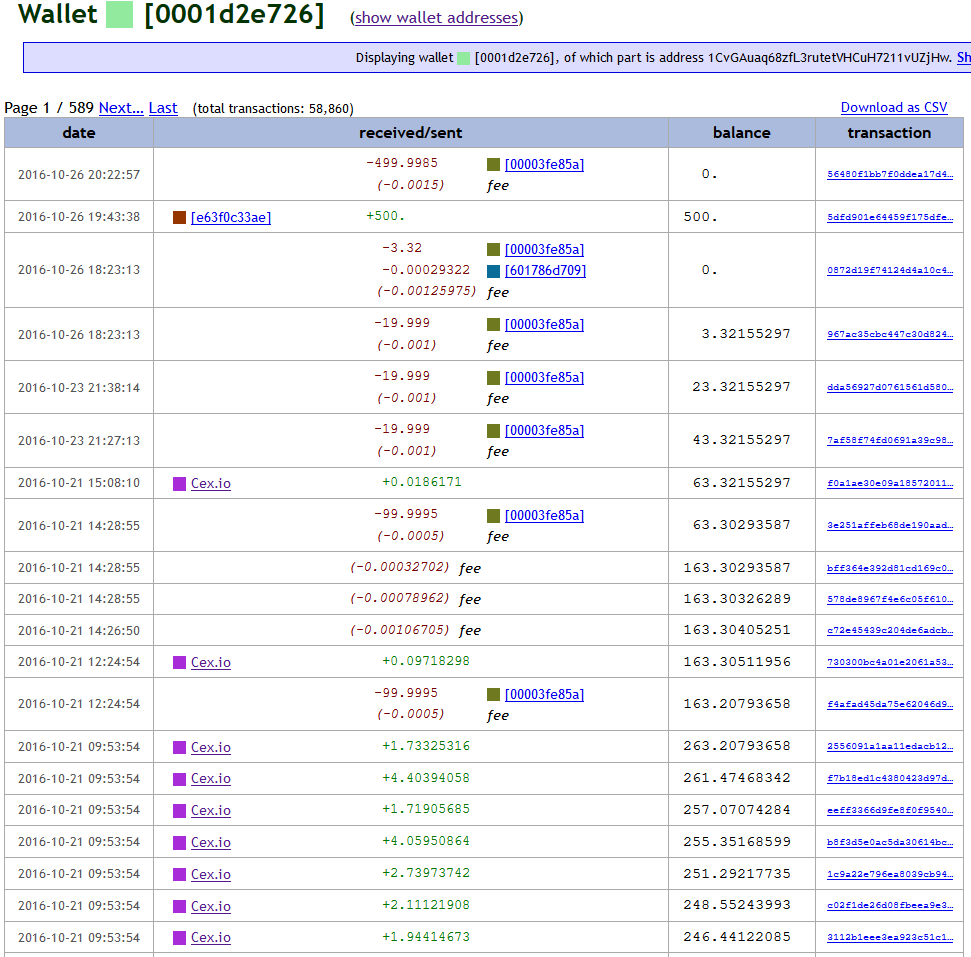
With reasonable certainty, we can therefore believe that the bitcoins were purchased through the Cex.io exchanger which, thanks to its KYC procedures, should be able to provide information on the customer who made the purchase or at least on the account used by who bought the bitcoins.
...to be continued...

September 28, 2020

Comments