Desktop-type wallets, like Electrum, create specific files which are needed to work correctly and store user information. In these files we can find information such as addresses included in the wallet, transactions carried out, information about the wallet type, etc. Obviously, given that this is very delicate information, these files are usually encrypted and cannot be consulted without knowing the correct password.
It may happen that we have to access a wallet for which we do not know the password, for example because we have forgotten it, or because we are trying to access the wallet of a "bad guy" during a digital forensics activity.
Our work enviroment
For today's example we will use Tsurugi Linux, a DFIR activity oriented distribution, which includes many carefully cataloged tools divided into categories, among which there is one named "Crypto Currency".
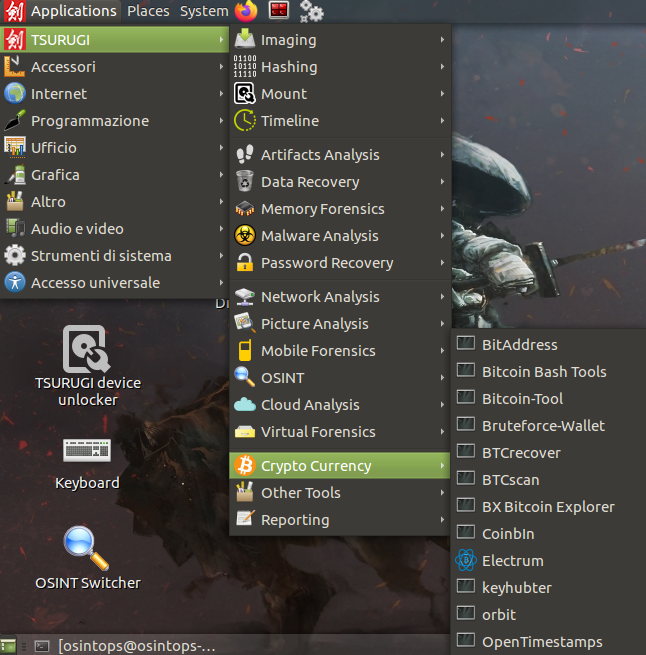
Let's assume we have already created a wallet with the Electrum client. If not, here you can find the official guide to create one. Electrum files, including the created wallets, are stored in a hidden folder inside the home directory.
To view them we can open the terminal and type the command
ls -a
The ls command is used to list the contents of the current folder, while the -a option is used to include hidden folders and files in the output.
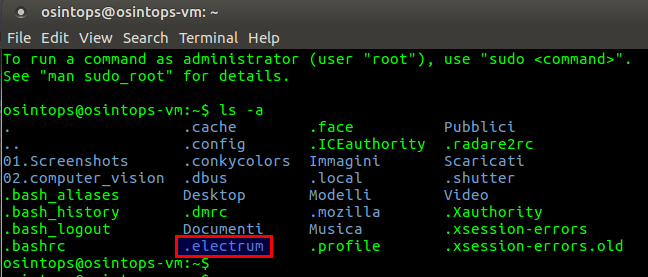
If we have already created a wallet with Electrum and everything went according to plan, we should see the .electrum folder. Inside we will find the wallets sub-folder, which will contain all the files relating to the wallets we have created.
Let's geto to know the tools
To try to recover access to a wallet, in our case created with Electrum, we will use the BTCrecover tool, present in the Tsurugi menu dedicated to Crypto Currency. In addition to the Bitcoin wallets created with Electrum, the tool is able to manage many other files, including wallets created with clients like Armory, MultiBit, Bither, etc. Obviously, the wallets do not need to be related to Bitcoin: they can also be related to other virtual currencies, managed by the clients supported by the tool.
When the tool is run, you must indicate the wallet file you want to open and a list of passwords to try. As an alternative to a list of passwords, it is possible to provide a list of words that are called tokens in the official guide, to create passwords made up of combinations of these words.
Let's get ready
In our example we will try to find the password of a wallet file named "default_wallet", a name that is suggested by Electrum's wizard during the creation phase.
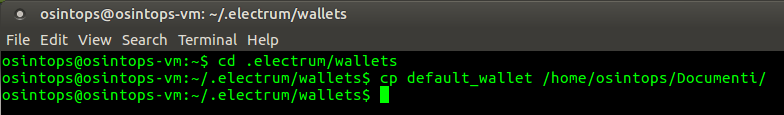
To avoid working directly on our file wallet, risking to damage it, let's start by creating a copy of the file, preferably in another workbook. First, using the command
cd .electrum/wallets
in our comman line terminal, we move to the folder where the file to be analyzed is stored. Then we copy the file to the Documents folder with the command
cp default_wallet /home/osintops/Documents/
Obviously instead of osintops you will have to use the username related to your work environment. You also have to use folder names corresponding to the language you set up on your Linux distro.
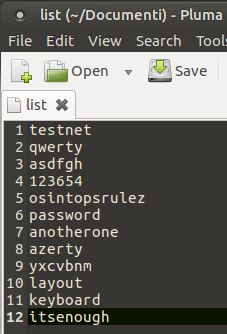
At this point, to try to open the wallet file, we will need a list of passwords. Online you can find many of various sizes, even several gigabytes. For our purposes, we just need to create a small text file containing some passwords including the right one and store it in the same folder where we copied the wallet to be opened.
Let's run the tool
Now that we have prepared what we need, we can run the BTCrecover tool. First let's go to the folder where we stored the copy of the wallet file to open and the list of passwords to try, in our case Documents. Let's use the command
cd ../../Documenti
The sequence ".." is used to return to the previous folder: first we went back to the .electrum folder, then to the home folder, and then we moved to the Documents folder.
At this point we can run the BTCrecover tool, with the command
btcrecover.py –wallet default_wallet –passwordlist list
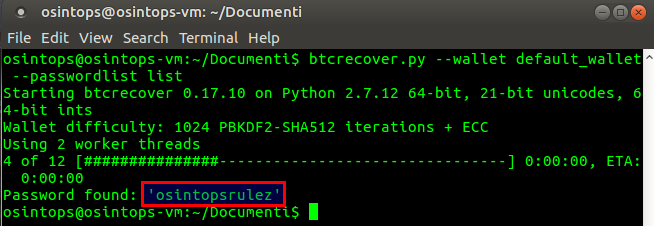
In a very short time (also due to the shortness of the list we've used), the tool managed to find the correct password to access the wallet. At this point, by opening the wallet through the Electrum client, it will be possible to view all the information on the history of the wallet, and to spend available bitcoins.
Final conclusions
We have seen how, using a couple of linux commands and an excellent tool, we can regain access to a wallet used for managing virtual currencies. In practice we have been able to observe that, by using the right tools, we can easily obtain very incisive results.
Let's imagine having a computer in front of us to analyze and being able to locate some file wallets. Using such a solution we could be able to access the bitcoinsof the "bad guy" and, if needed, we could also try to seize them.

September 28, 2020

Comments