It's quite common to run Google searches for OSINT purposes, so we need to find a way to make it fast, simple and easy. Moreover, we want (need) to spend our time focusing on the actual analysis rather than just grabbing data to analyze.
As a matter of fact, having a good way to grab data is a good starting point, but not enough. We also need to deal with it avoiding possible troubles, integrating it with our databases and/or analysis tools.
In this article I'll show you my personal way to run Google searches (including dorks) on Maltego, which is one of the most known and popular graphical link analysis tools used by Law Enforcement Officers/Agents, researchers, journalists and OSINT practitioners in general.
Setup
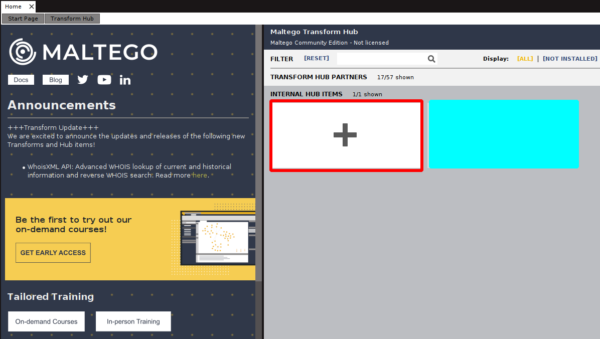
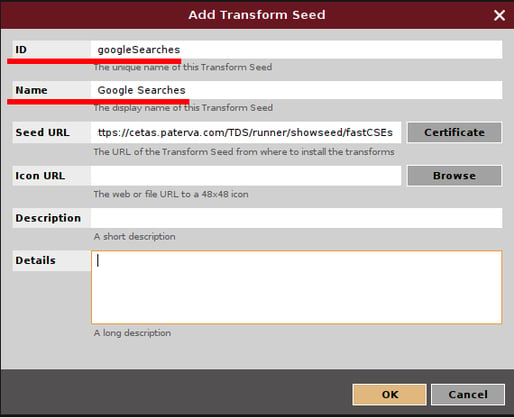
The first step is to have Maltego up and running, the community edition is enough. The set of remote transforms I'll share you is completely free and un-metered. At this point all you have to do is to add the set of transforms with this link as seedhttps://cetas.paterva.com/TDS/runner/showseed/fastCSEs as shown in the screenshots below:
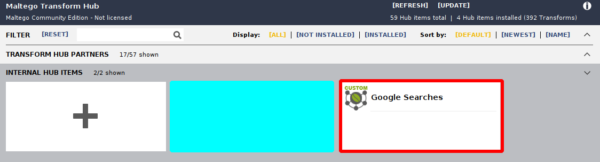
After clicking "OK" you should have a new entry in your "Internal Hub Items" tab:
The final step is to click on "Install" to actually add the transforms to your Maltego instance.
Even if the client-side of the transforms doesn't change quite often, remember to click on "Refresh" from time to time, to have the latest updates.
At this point the setup is completed, now we can play with it.
Usage
All that you have to know is that each transform accepts "Phrase" entities.
It's as simple as:
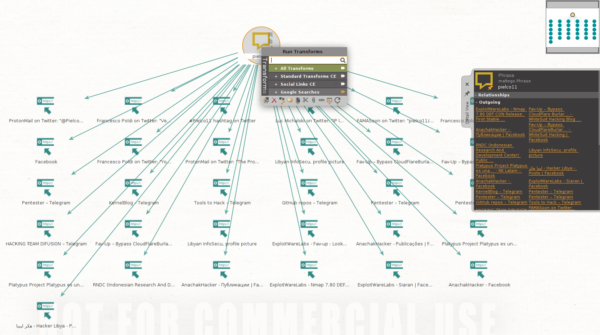
- grab the Phrase item from the Entity Palette (Person tab)
- fill the "Text" property with your search query
- right click on the entity and execute the transform
At the time of writing only the following social networks are supported:
- 4Chan
- 8Chan
- Dailymotion
- Gab
- Telegram
- VKontakte
- YouTube
What if we want to restrict our search for a given context and thus return intelligence of a higher quality? Google Dorks!
(I'd like to recall you that intelligence can simply be defined as information in a given context.)
Real World Usage
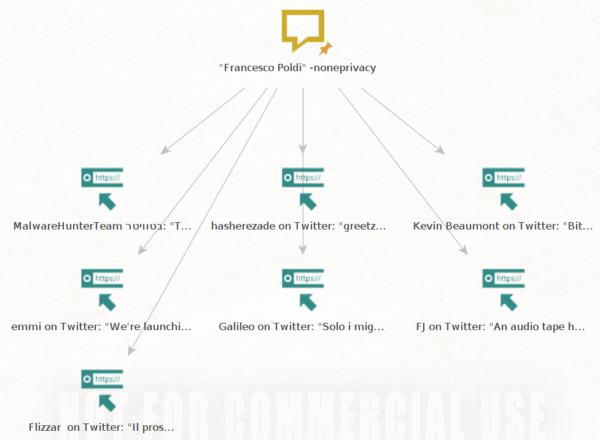
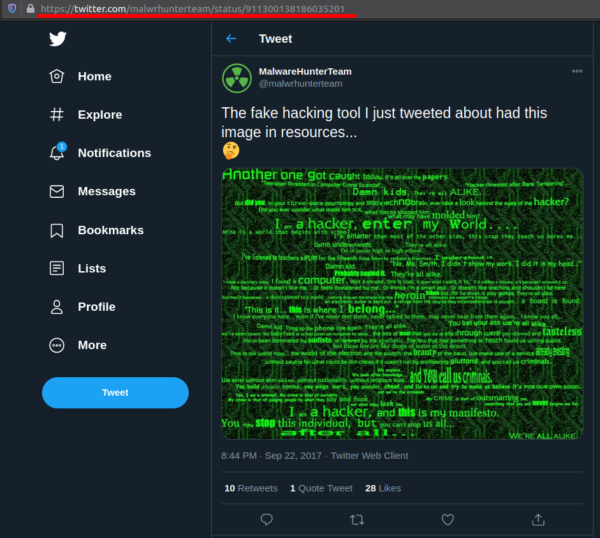
In the next example I'll use myself as a target and specifically I'm going to search for my previous Twitter handle. So what I have to do is to search for my full name as keyword and remove my current Twitter handle, then the query looks like this "Francesco Poldi" -noneprivacy
Usually we don't get such a few results, so a finer DORK might be required. Fortunately we can just stop here and start looking at the results.
Final step is to look at each of those and see which one may provide helpful information.
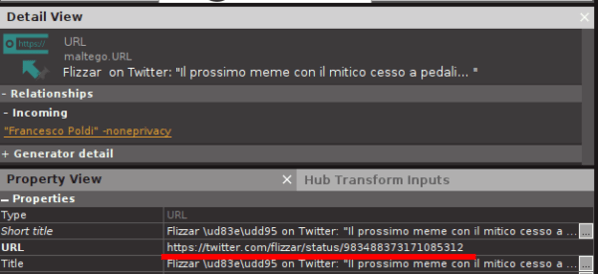
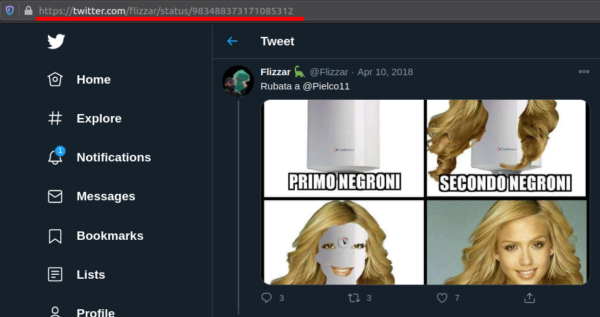
At first glance you may conclude that only one of those tweets is useful because the first one of the thread contains the mention @Pielco11.
Going Deeper
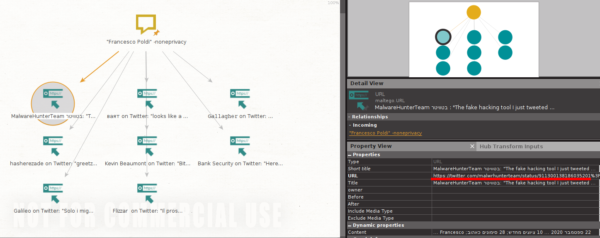
So what about the others? Is Google wrong? Is the transform wrong? Are we actually missing something?
Fortunately, or not, we are actually missing something. Why? There are two answers:
- we are looking for mentions and text in the tweet, but that's not how Google works
- we still need to justify the other returned results
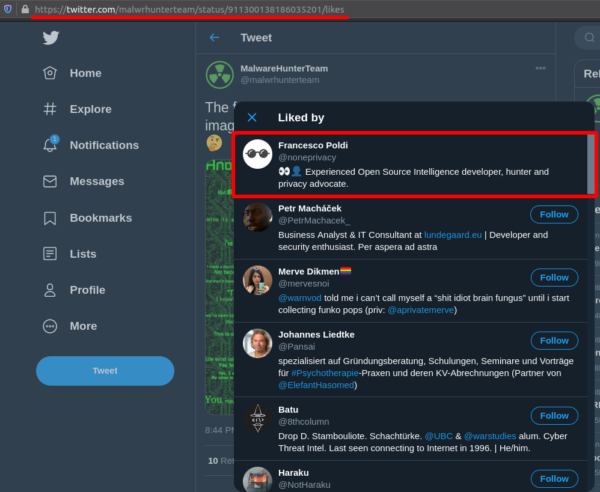
As you may guess, those two answers are different but connected somehow. The crucial point is that on Twitter users send tweets, but also "like" tweets and re-tweet contents. Google returns you tweets matching the query for the text field, and tweets liked and/or retweeted by users.
Those tweets were liked/retweeted by me before and after changing my handle, and this is gold when you have to chrono-locate the association of an user to a given handle (thus enriching the context). For example, we can use the timestamp of the tweet which contains my previous Twitter handle and use it to restrict searches within Twitter and outside of it.
What's for sure is that I did also "like" other tweets and not all of those appear, but remember that knowing who liked what and which tweets were liked by who is quite challenging, especially if you are not logged in.

January 12, 2021

Comments