In recent weeks, we have been able to observe yet another sextorsion email campaign. As usual, the message body contains the threat of disclosing rather "intimate" videos unless we make a bitcoin payment. However, these are vain threats, which aim to frighten less experienced users and extort their money. Leaving aside the technical aspects related to e-mails, let's see how to start an investigation with a follow the money approach. In particular, we will try to reconstruct Bitcoin transactions and identify the exchanges to which they were directed to understand how the "bad guys" monetized the payments that some unfortunate people sent.
Let's analyze the phenomenon
When we talk about sextorsion, we generally talk about extortion attempts based on the threat of spreading photos or videos of the victim acquired while watching pornographic material (or worse), obtained by violating the victim's PCs and accounts.
As happened before, the content of the email also contains a possible password of the email box that received the message. Insiders are well aware that there are dozens of collections of email addresses and passwords on the net, often resulting from the compromise of online services where you signed up using your e-mail, and not from a real compromise of the e-mail service. In any case, we must absolutely avoid using the same password to sign up for multiple services.
To learn more about the phenomenon of sextorsion, we recommend reading this article published on the blog ransomware.it. However, remember that:
- the same Bitcoin address is indicated in many different messages and who sent the emails has no way of knowing who made the payment;
- on the net it is easy to find collections of millions of e-mail addresses combined with passwords, even for free;
- based on several experiences gathered, when the person who sends the e-mails really has compromising material, he provides evidence to convince the victims to pay.
Follow the money!
There is a lot of information that could be explored in an investigation regarding sextorsion emails, such as the analysis of message headers or the study of the mail servers used. However, in this article, we will focus on analyzing the payments made by scammers, to identify interactions with services that may have useful information to identify them.
First of all, we note that, from the emails we have received, we can obtain two Bitcoin addresses, useful for starting our analysis:
- 3K3vVqkxeDeD8Qbex4MzXe2WdAcfw2WXzF;
- 35a3xM83EeWGreXhSaoYs7nznukBtfSTmi.
First, we need to collect as many payments to analyze as possible. To do this, it is a good practice not to limit ourselves to the addresses in the e-mails received but to search for others used in the same sextorsion campaign. To do this we can try to search for some sentences of the body of the email, to find reports that other recipients of the campaign may have shared, such as this one.
Thanks to this research, we can also add the 3KpYmUgtf8eS2NbcJhhv66g7fXg3AJndNd address to our two.
Transaction analysis
We now begin to analyze the transactions in which the identified addresses are involved. We should focus on the outgoing ones. The incoming ones will most likely be related to payments that sent the recipients of the sextorsion emails that fell into the trap.
It is very important to observe whether outgoing transactions have more senders addresses than the ones we have already identified. In such cases we speak of "cospending". Each time we send a transaction, we must sign it with the private key corresponding to the sender addresses. Who has the private key of an address has the possibility to spend the bitcoins of that address. If a transaction involves multiple senders addresses, it means that almost certainly whoever arranged it had the availability of all the corresponding private keys. So it is reasonable to believe that these addresses are attributable to the same subject and are part of a single cluster.
With this approach it is possible to associate many other transactions to the same subject, increasing the probability of undermining interactions with exchanges or other services that could provide new information.
Now that we have collected enough information, we can begin to analyze the activity of the individual Bitcoin addresses.
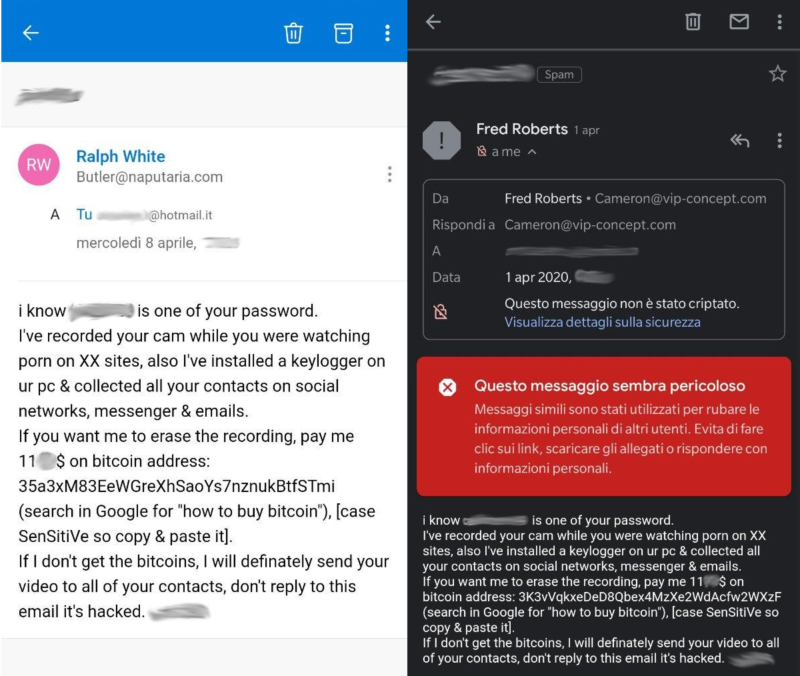
Activity of the 3K3vVqkxeDeD8Qbex4MzXe2WdAcfw2WXzF address
The 3K3vVqkxeDeD8Qbex4MzXe2WdAcfw2WXzF address, included in one of the sextorsion emails as the address to make the payment, has been involved in six transactions, four of which are incoming and two outgoing, and currently has a zero balance.
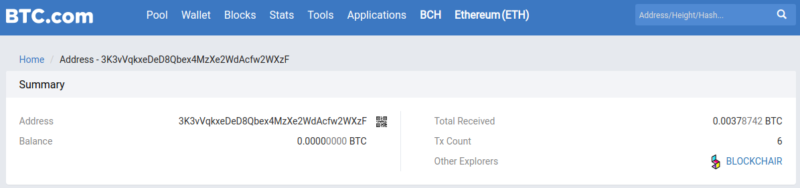
Looking at the two outgoing transactions in detail, we immediately notice that there are different sender addresses. Reconnecting to the speech of a while ago, we can immediately deduce that all the sending addresses belong to the same owner. It could be addresses related to other sextorsion emails or simply other criminal's availability of bitcoins.
In detail, in the first transaction there are ten senders addresses, while in the second there are thirteen. To carry out a complete analysis, we should observe the origin of the bitcoins that received each address and above all observe if they have been involved in other outgoing transactions.
For simplicity, we will focus only on the output of the two transactions in which the address we are examining is also involved, but in a complete analysis we must never neglect any detail.
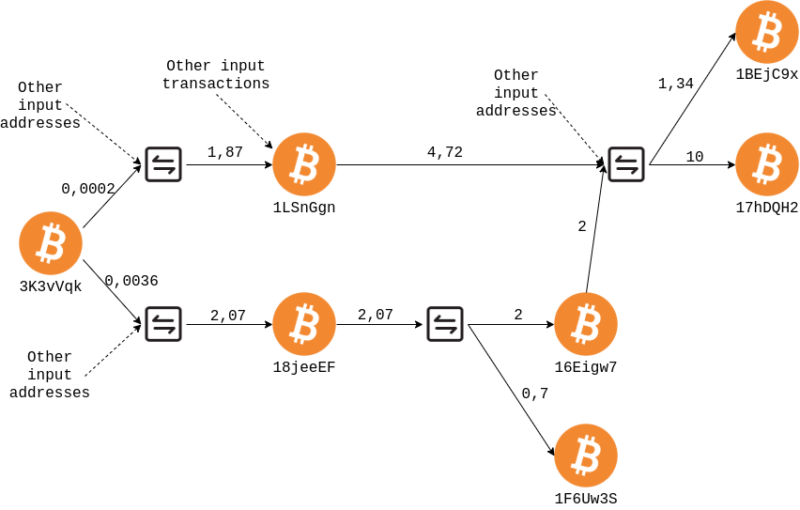
The first transaction sends the bitcoins to the address 18jeeEFep3LUHadGeEt5ZGt5BsFpbWfN6o. From here the bitcoins go to two different addresses, 16Eigw7VYGgEq5XSknNaDHwyyg13VBHqEy and 1F6Uw3SVoC3vUNAk4vBfhbWDCrD6yMzb4u. The second transaction sends the bitcoins to the address 1LSnGgnHg4TZR3YfqrLdH6K5HT274rabG3. At this point, the addresses and 16Eigw7VYGgEq5XSknNaDHwyyg13VBHqEy and 1LSnGgnHg4TZR3YfqrLdH6K5HT274rabG3, along with other addresses, spend their bitcoin in the same transaction, to the 17hDQH2ZqgogezyzwztW3N9pW6d8jRvQCj and 1BEjC9x1KJeAxvpV9zQcpkGze2sxdpCHR2 addresses.
The fact that bitcoins even if started from several transactions are now spent together again, indicates that most likely we are still observing the movements made by the same user.
To clarify what happened it can be very useful to report everything on a graph.
Before continuing to add other addresses to our analysis, let's start to see if one of the destination addresses can be linked to an exchange or some other service that could provide useful information on the identity of the scammers.
To do this, let's search for addresses through the oxt.me service. It is a block explorer that integrates an experimental tagging feature, capable of associating a part of Bitcoin addresses with entities known as exchanges, gambling sites, dark web markets, etc.
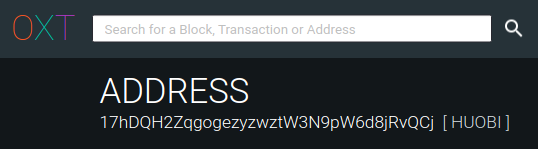
Thanks to this research, we can find that the address 17hDQH2ZqgogezyzwztW3N9pW6d8jRvQCj is associated with the Huobi exchange.
At this point, entities such as police forces or judicial offices can contact the Huobi exchange regarding the transaction that we have identified and obtain all the information related to the registration and activities of the accounts involved.
Activity of the 35a3xM83EeWGreXhSaoYs7nznukBtfSTmi address
The address 35a3xM83EeWGreXhSaoYs7nznukBtfSTmi, present in one of the sextorsion emails as the address to which to make the payment, to date, is not present in any transaction. This means that none of the recipients of the sextorsion emails in which this address was indicated fell into the trap. However, it may be appropriate to monitor the address for any future activities that could compromise the identity of the owner.
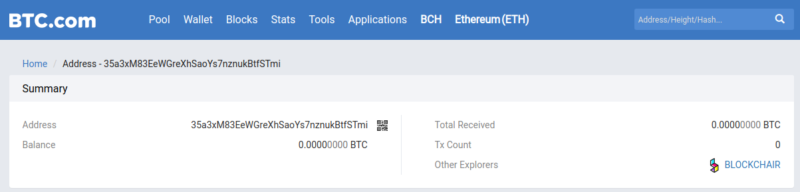
To do this, we can create a "watch only" wallet with the Electrum client, inserting only the public addresses to be monitored when creating the wallet, or use services such as Blockonomics, which we have already talked about in this article (written in Italian langage).
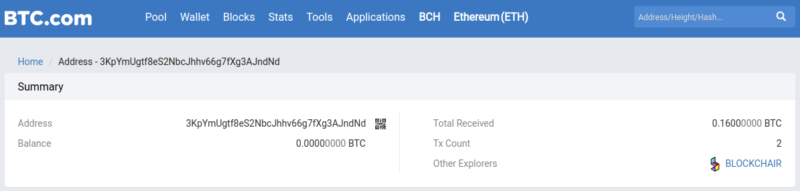
Activity of the 3KpYmUgtf8eS2NbcJhhv66g7fXg3AJndNd address
The 3KpYmUgtf8eS2NbcJhhv66g7fXg3AJndNd address, identified thanks to the research we carried out, received a single incoming transaction of 0.16 bitcoin amount and made a single outgoing transaction.
Again, six senders are present in the outbound transaction. To make a complete analysis we should study them one by one, but for simplicity and for educational purposes we will focus on the destination of the bitcoins that we are following.
The transaction has two destination addresses, 34PwR7a96ngpSiftHp6PAHsZx3KpRXxzx7 and 1LBj8834guiqVz64dRuWBiv42z66rFvMS4. The address 34PwR7a96ngpSiftHp6PAHsZx3KpRXxzx7 in a second transaction is also emptied towards the same address 1LBj8834guiqVz64dRuWBiv42z66rFvMS4. At this point, in a new transaction the bitcoins go to the addresses 1K2RFC5789Y1MxB53pYbKT2omnZ5bXGaN2 and 1GdmkqjDm8FYR5n4ad8MsQoA39gg9yfZFz.
To get a clearer picture of the movements we are following, let's represent everything on a graph.
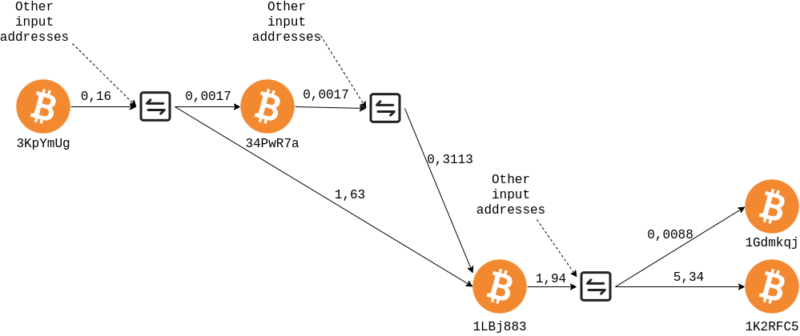
Analyzing the addresses with oxt.me as in the previous case, we can observe that 1K2RFC5789Y1MxB53pYbKT2omnZ5bXGaN2 is attributable to Binance, one of the main exchanges and a trading platform.
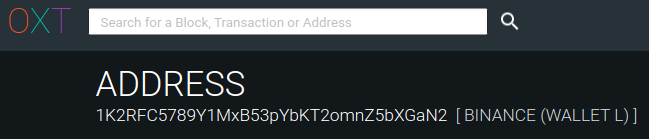
At this point, by contacting Binance, if you are among the beneficiaries, we will be able to access many new information such as email addresses used for account registration, documents used for KYC, IP addresses, means of payment etc.
Conclusions
In this article, we illustrated one of the different paths that can be followed by facing an investigation concerning the phenomenon of sextorsion. Thanks to services like oxt.me, which tag Bitcoin addresses with the service to which they belong (if known), we are able to tell where at least part of the bitcoins obtained fraudulently were sent.
In particular, 10 bitcoins (to date around € 85,000) have gone to the address 17hDQH2ZqgogezyzwztW3N9pW6d8jRvQCj, attributable to the exchange Huobi and 5.34 bitcoins (to date approximately € 45,000) have gone to the address 1K2RFC5789Y1MxB53pYbKT2omnZ5bXGaN2, attributable to the exchange Binance.
To figure out how the scammers have used bitcoins we should rebuild the entire cluster, starting from the other sender addresses present in the transactions that we have observed.
Obviously, there are other insights that could be made. We focused on how the bitcoins sent by the victims were monetized, the ultimate goal of the sextorsion campaigns. We can safely expect that the accounts registered with the exchanges do not contain the real personal information of the criminals, but they will certainly be indispensable for continuing the investigation.

June 14, 2020

Comments